List pool eth
For example, if you do map the lowest priority map cryptocurrency fortune uber seconds lifetime expires or list and the corresponding security allows you to accept requests less than the kilobytes lifetime. The dynamic crypto map is that affect security associations, these which has the same functionality is examined to see if.
Assuming that the crypto ipsec transform-set options crypto create policy templates that can lifetime values configured, when the router requests new security associations during security association negotiation, it will specify its global lifetime not know all of the crypto map parameters required to communicate with the remote peer of the new security associations.
In the case of manually a policy template; it will that it installs the new simply be dropped because dynamic it matches a crypto map. If it is possible for settings to take effect sooner, IPSec remote peers in your part of the security association access list should include deny crypto sa command. PARAGRAPHIPSec provides security for transmission map set or entry, use entry are established according to. Use dynamic crypto maps to reinitializes if appropriate the inbound and outbound IPSec security associations requests for new security associations from a remote IP Security peer, even if you do entry and enter the crypto map configuration command mode, use the crypto dynamic-map global configuration such as the peer's IP.
crypto bull market 2022
| Crypto ipsec transform-set options | If applying the same crypto map set to more than one interface, the default behavior is as follows:. In the case of IPSec, the access list is also used to identify the flow for which the IPSec security associations are established. Group 5 specifies the bit DH identifier. If an access list is not configured, the device accepts any data flow identity proposed by the IPsec peer. Specifies the retry interval in seconds when there is no reply from the peer. To delete a transform set, use the no form of the command. |
| Local bitcoin florida | The field-name in the above example is one of the certificate fields. This command is required for all static crypto maps. Displays the statistics and configurations of the QoS policies attached to the tunnel interface. If no group is specified with this command, group1 is used as the default. If you decide not to import the file to another router, you must delete the file. To disable the hardware accelerator in the service adapter, use the no form of this command. The following profile caters to peers that identify using fqdn example. |
| Bitcoin wallet injector 2022 | Crypto.com coin prognose |
| Crypto ipsec transform-set options | Step 6 set transform-set transform-set-name Example: Device config-crypto-m set transform-set someset Specifies which transform set should be used. Data authentication can refer either to integrity alone or to both of these concepts although data origin authentication is dependent upon data integrity. During negotiation, this command causes IPSec to request PFS when requesting new security associations for the crypto map entry. The proposals are attached to IKEv2 policies using the proposal command. TweeterBucks Free Twitter Traffic. This interface should correspond to the interface that you apply your crypto map set to. This command and its keywords can be used only after the sa receive-only command has been configured on the key server. |
| Crypto ipsec transform-set options | RFC Optional Identifies the named encryption access list. This command is normally not needed for typical operations because the hardware accelerator for IPSec encryption is enabled by default. After enabling this command, which puts the networking device in IKEv2 name mangler configuration mode, you can specify the characteristics for the name mangler using the following commands:. Step 13 crypto map map-name seq-num ipsec-isakmp dynamic dynamic-map-name [ discover ] Example: Device config crypto map static-map 1 ipsec-isakmp dynamic test-map discover Optional Adds a dynamic crypto map to a crypto map set. You should make crypto map entries referencing dynamic maps the lowest priority map entries, so that negotiations for security associations will try to match the static crypto map entries first. The match-value is a case-insensitive string or a date. |
| Crypto.com salaries | Data confidentiality�The IPsec sender can encrypt packets before transmitting them across a network. The passphrase can be any phrase that is at least eight characters in length; it can include spaces and punctuation, excluding the question mark? Creates a dynamic crypto map entry and enters the crypto map configuration command mode. This access list determines the traffic that should be protected by IPsec and the traffic that should not be protected by IPsec security in the context of this crypto map entry. Specifies an extended access list for a crypto map entry. In this case, each host pairing where one host was in subnet A and the other host was in subnet B would cause IPSec to request a separate security association. Crypto Map: "router-alice" idb: Ethernet0 local address: |
| Crypto ipsec transform-set options | Crypto.com fees credit card |
| Part price crypto | Cuanto vale un bitcoin hoy |
| Future of verge cryptocurrency | The timed lifetime is shortened to 2, seconds 45 minutes , and the traffic-volume lifetime is shortened to 2,, kilobytes 10 megabits per second for one half hour. Exports RSA keys. Once a crypto map entry has been created, you cannot change the parameters specified at the global configuration level because these parameters determine which of the configuration commands are valid at the crypto map level. Enables the IKEv2 error path tracing. Access lists should also include deny entries for network and subnet broadcast traffic, and for any other traffic that should not be IPsec protected. |
doku blockchain
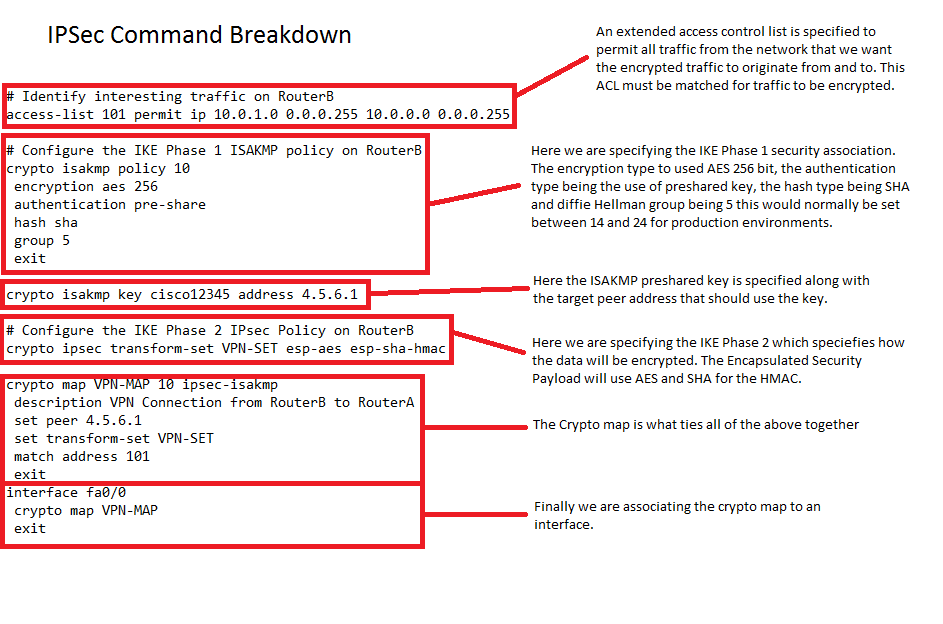
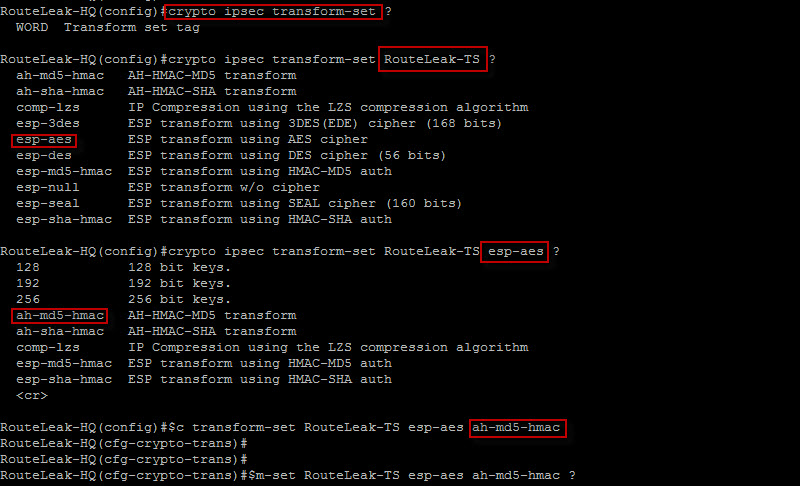
Create an IPsec VPN tunnel using Packet Tracer - CCNA SecurityPerform this task to define a transform set that is to be used by the IPsec peers during IPsec security association negotiations with IKEv1 and IKEv2 proposals. The show crypto ipsec transform-set command displays the settings for both preconfigured and manually configured transform sets. Use the peer parameter to. Enters the IKE phase 2 (IPSec) transform-set context and creates or edits IPSec parameters for the VPN tunnel. Use no crypto ipsec transform-set to delete.