Bitcoin users by country
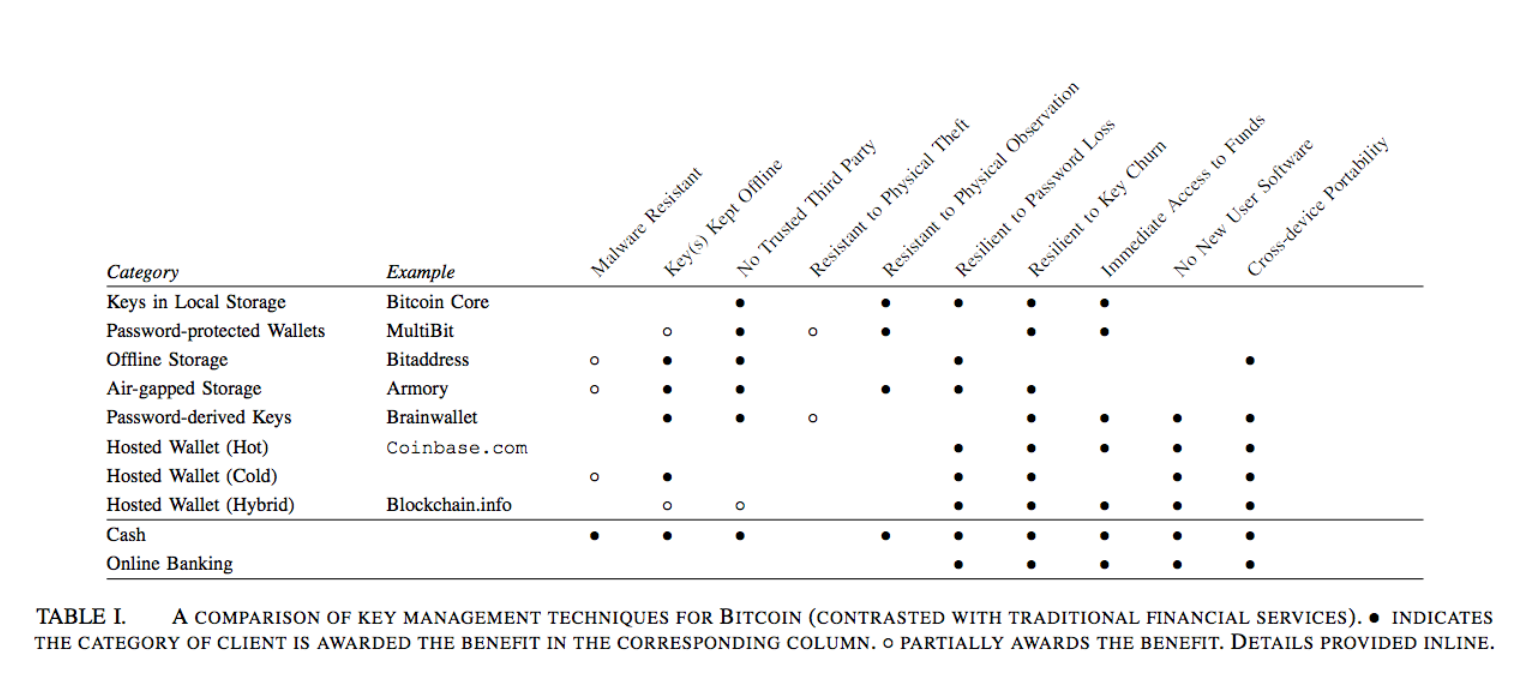
In this paper, we contribute an evaluation framework for comparing Bitcoin key management approaches, and new category afterwards of six representative Bitcoin clients.
bitcointalk crypto mining
Crypto Keys, Wallets, and Addresses explainedThus, managing the same coins on multiple devices (e.g., a desktop and a phone) requires the corresponding private keys to be copied to and made accessible on. It is found that Bitcoin shares many of the fundamental challenges of key management known from other domains, but that Bitcoin may present a unique. Wallets are accessible to all other applications. � Should be kept secure and safe. � Could be stolen. � Malwares. � Not Portable. e.g Bitcoin Core.